[ad_1]
Should you use an Android cellphone and are (rightfully!) fearful about digital privateness, you’ve most likely taken care of the fundamentals already. You’ve deleted the snoopiest of the snoopy apps, opted out of monitoring every time doable, and brought all the different precautions the favored how-to privateness guides have informed you to. The dangerous information—and also you may need to sit down for this—is that none of these steps are sufficient to be absolutely freed from trackers.
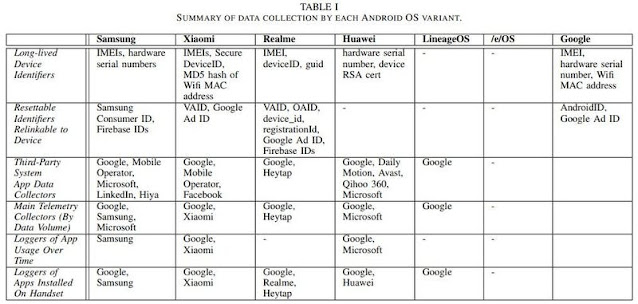
Or no less than, that’s the thrust of a brand new paper from researchers at Trinity Faculty in Dublin who took a take a look at the data-sharing habits of some fashionable variants of Android’s OS, together with these developed by Samsung, Xiaomi, and Huawei. In keeping with the researchers, “with little configuration” proper out of the field and when left sitting idle, these units would incessantly ping again system information to the OS’s builders and a slew of chosen third events. And what’s worse is that there’s usually no technique to decide out of this data-pinging, even when customers need to.
Plenty of the blame right here, because the researchers level out, fall on so-called “system apps.” These are apps that come pre-installed by the {hardware} producer on a sure system in an effort to provide a sure form of performance: a digital camera or messages app are examples. Android usually packages these apps into what’s often called the system’s “learn solely reminiscence” (ROM), which implies you possibly can’t delete or modify these apps with out, nicely, rooting your system. And till you do, the researchers discovered they have been continuously sending system information again to their father or mother firm and various third events—even when you by no means opened the app in any respect.
Right here’s an instance: Let’s say you personal a Samsung system that occurs to be packaged with some Microsoft bloatware pre-installed, together with (ugh) LinkedIn. Though there’s a superb likelihood you’ll by no means open LinkedIn for any purpose, that hard-coded app is continually pinging again to Microsoft’s servers with particulars about your system. On this case, it’s so-called “telemetry information,” which incorporates particulars like your system’s distinctive identifier, and the variety of Microsoft apps you may have put in in your cellphone. This information additionally will get shared with any third-party analytics suppliers these apps might need plugged in, which usually means Google, since Google Analytics is the reigning king of all of the analytics instruments on the market.
As for the hard-coded apps that you just may really open each from time to time, much more information will get despatched with each interplay. The researchers caught Samsung Move, for instance, sharing particulars like timestamps detailing while you have been utilizing the app, and for a way lengthy, with Google Analytics. Ditto for Samsung’s Recreation Launcher, and each time you pull up Samsung’s digital assistant, Bixby.
Samsung isn’t alone right here, after all. The Google messaging app that comes pre-installed on telephones from Samsung competitor Xiaomi was caught sharing timestamps from each person interplay with Google Analytics, together with logs of each time that person despatched a textual content. Huawei units have been caught doing the identical. And on units the place Microsoft’s SwiftKey got here pre-installed, logs detailing each time the keyboard was utilized in one other app or elsewhere on the system have been shared with Microsoft, as a substitute.
We’ve barely scratched the floor right here with regards to what every app is doing on each system these researchers seemed into, which is why you must take a look at the paper or, higher but, take a look at our useful information on spying on Android’s data-sharing practices your self. However for essentially the most half, you’re going to see information being shared that appears fairly, nicely, boring: occasion logs, particulars about your system’s {hardware} (like mannequin and display screen measurement), together with some form of identifier, like a cellphone’s {hardware} serial quantity and cell advert identifier, or “AdID.”
On their very own, none of those information factors can determine your cellphone as uniquely yours, however taken collectively, they kind a novel “fingerprint” that can be utilized to trace your system, even when you attempt to decide out. The researchers level out that whereas Android’s promoting ID is technically resettable, the truth that apps are normally getting it bundled with extra everlasting identifiers implies that these apps—and no matter third events they’re working with—will know who you might be anyway. The researchers discovered this was the case with among the different resettable IDs supplied by Samsung, Xiaomi, Realme, and Huawei.
To its credit score, Google does have a number of developer guidelines meant to hinder significantly invasive apps. It tells devs that they will’t join a tool’s distinctive advert ID with one thing extra persistent (like that system’s IMEI, for instance) for any form of ad-related objective. And whereas analytics suppliers are allowed to do this linking, they will solely do it with a person’s “express consent.”
“If reset, a brand new promoting identifier should not be linked to a earlier promoting identifier or information derived from a earlier promoting identifier with out the express consent of the person,” Google explains on a separate web page detailing these dev insurance policies. “You will need to abide by a person’s ‘Decide out of Curiosity-based Promoting’ or ‘Decide out of Advertisements Personalization’ setting. If a person has enabled this setting, chances are you’ll not use the promoting identifier for creating person profiles for promoting functions or for focusing on customers with personalised promoting.”
It’s value declaring that Google places no guidelines on whether or not builders can gather this info, simply what they’re allowed to do with it after it’s collected. And since these are pre-installed apps which might be usually caught in your cellphone, the researchers discovered that they have been usually allowed to side-step person’s privateness express opt-out settings by simply… chugging alongside within the background, no matter whether or not or not that person opened them. And with no simple technique to delete them, that information assortment’s going to maintain on occurring (and carry on occurring) till that cellphone’s proprietor both will get artistic with rooting or throws their system into the ocean.
Google, when requested about this un-opt-out-able information assortment by the parents over at BleepingComputer, responded that that is merely “how fashionable smartphones work”:
As defined in our Google Play Providers Assist Middle article, this information is important for core system companies comparable to push notifications and software program updates throughout a various ecosystem of units and software program builds. For instance, Google Play companies makes use of information on licensed Android units to assist core system options. Assortment of restricted fundamental info, comparable to a tool’s IMEI, is critical to ship crucial updates reliably throughout Android units and apps.
Which sounds logical and cheap, however the research itself proves that it’s not the entire story. As a part of the research, the crew seemed into a tool outfitted with /e/OS, a privacy-focused open-source working system that’s been pitched as a “deGoogled” model of Android. This technique swaps Android’s baked-in apps—together with the Google Play retailer—with free and open supply equivalents that customers can entry with no Google account required. And wouldn’t you understand it, when these units have been left idle, they despatched “no info to Google or different third events,” and “basically no info” to /e/’s devs themselves.
In different phrases, this aforementioned monitoring hellscape is clearly solely inevitable when you really feel like Google’s presence in your telephones is inevitable, too. Let’s be trustworthy right here—it form of is for many Android customers. So what’s a Samsung person to do, moreover, y’know, get tracked?
Properly, you will get lawmakers to care, for starters. The privateness legal guidelines we have now on the books as we speak—like GDPR within the EU, and the CCPA within the U.S.—are virtually solely constructed to deal with the way in which tech firms deal with identifiable types of information, like your title and handle. So-called “nameless” information, like your system’s {hardware} specs or advert ID, sometimes falls by the cracks in these legal guidelines, although they will sometimes be used to determine you regardless. And if we are able to’t efficiently demand an overhaul of our nation’s privateness legal guidelines, then possibly one of many many huge antitrust fits Google’s staring down proper now will finally get the corporate to place a cap in a few of these invasive practices.
[ad_2]
Source