[ad_1]

The Lithuanian Nationwide Cyber Safety Centre (NCSC) lately revealed a safety assessment of three recent-model Chinese language-made smartphones—Huawei’s P40 5G, Xiaomi’s Mi 10T 5G, and OnePlus’ 8T 5G. Sufficiently decided US buyers can discover the P40 5G on Amazon and the Mi 10T 5G on Walmart.com—however we is not going to be offering direct hyperlinks to these telephones, given the outcomes of the NCSC’s safety audit.
The Xiaomi cellphone consists of software program modules particularly designed to leak information to Chinese language authorities and to censor media associated to subjects the Chinese language authorities considers delicate. The Huawei cellphone replaces the usual Google Play utility retailer with third-party substitutes the NCSC discovered to harbor sketchy, doubtlessly malicious repackaging of widespread functions.
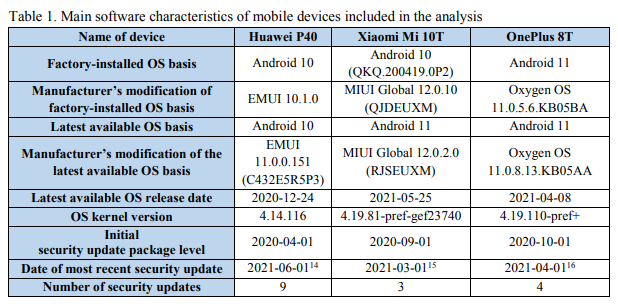
Huawei’s P40 continues to be caught on Android 10, whereas Xiaomi ships with 10 however will be upgraded to 11. Solely the OnePlus 8T shipped from the manufacturing unit with Android 11 put in.
The OnePlus 8T 5G—arguably, the best-known and most generally marketed cellphone of the three—was the one one to flee the NCSC’s scrutiny with none purple flags raised.
Xiaomi Mi 10T 5G
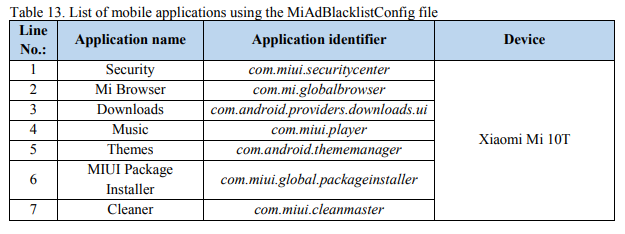
The NCSC discovered that seven default system apps on the Xiaomi cellphone can monitor media content material for blocking from the consumer, utilizing a commonly downloaded JSON file.
Xiaomi’s Mi 10T 5G ships with a nonstandard browser referred to as “Mi Browser.” The NCSC discovered two elements in Mi Browser which it did not like—Google Analytics, and a much less acquainted module referred to as Sensor Knowledge.
The Google Analytics module in Mi Browser can learn from the gadget’s looking and search historical past and may then ship that information to Xiaomi servers for unspecified evaluation and use. The Google Analytics module is activated routinely by default through the cellphone’s first activation or after any manufacturing unit reset.
The NCSC discovered that Sensor Knowledge’s module collects statistics on 61 parameters associated to utility exercise, together with time of app activation, language used, and so forth. These statistics are encrypted and despatched to Xiaomi servers in Singapore, a rustic which the NCSC notes just isn’t lined by the EU’s GDPR and has been tied to excessive information assortment and abuse of consumer privateness.
The NCSC additionally discovered that the consumer’s cell phone quantity is silently registered to servers in Singapore through encrypted SMS message on activation of default Xiaomi cloud companies. The cell phone quantity is shipped whether or not the consumer ties it to a brand new cloud account or not, and the encrypted SMS just isn’t seen to the consumer.
A number of of the Xiaomi system functions on the Mi 10T 5G commonly obtain a file referred to as MiAdBlackListConfig from servers in Singapore. On this file, the NCSC discovered 449 data figuring out non secular, political, and social teams. Software program courses in these Xiaomi functions use MiAdBlackListConfig to investigate multimedia which may be displayed on the gadget and block that content material if “undesirable” key phrases are related to it.
Though the NCSC found that the precise content material filtering through MiAdBlackListConfig is disabled on telephones registered within the European Union, the telephones nonetheless commonly obtain the blocklist itself—and, the company says, will be remotely reactivated at any time.
Huawei P40 5G
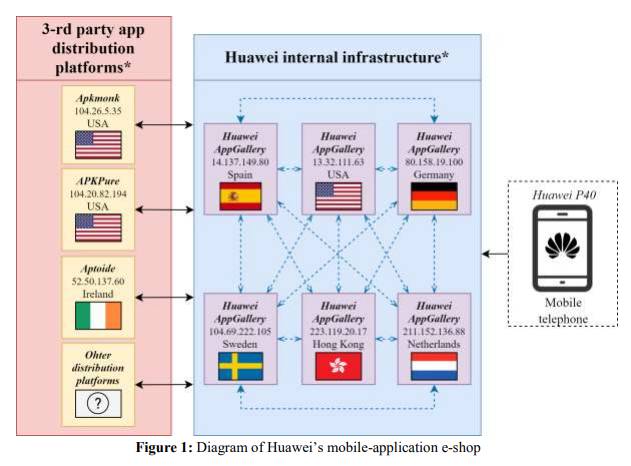
The NCSC discovered that customers who seek for functions in Huawei’s AppGallery are sometimes redirected to doubtlessly untrustworthy third-party repositories.
Though the NCSC didn’t discover the identical class of adware and content-filtering modules in Huawei’s P40 5G because it had within the Mi 10T 5G, it nonetheless wasn’t pleased with the cellphone’s software program infrastructure—and for good cause.
The P40 5G’s most blatant issues stem from its substitute of Google’s Play Retailer with Huawei’s personal AppGallery retailer, which it payments as “a safer place to get all of your favourite apps.” The NCSC discovered that, if a consumer searches AppGallery for a specific utility, they are going to be silently redirected to third-party app shops if no match is present in AppGallery itself.
Third-party distribution platforms the NCSC discovered linked to AppGallery embody however will not be restricted to Apkmonk, APKPure, and Aptoide. The NCSC used VirusTotal to scan a number of apps put in through AppGallery and its linked third-party platforms, and it found potential malware on three: All in One social media, CNC Machinist Tapping Calculator, and “Messenger app, Gentle All-in-One, Dwell Free Chat Professional App.”
We’re not sure how a lot salt to take with the NCSC’s particular “malware” findings for the reason that company didn’t reverse engineer any of the three apps VirusTotal did not like—and antivirus false positives on much less well-known apps occur with some regularity. Nevertheless, the apparently silent linking from AppGallery to third-party app shops does introduce a real threat of gadget compromise.
Though Apkmonk, APKPure, and Aptoide are all fairly well-known “alternate shops,” they’re much less completely curated than Google’s personal Play Retailer. Aptoide, for instance, affords each its personal most important repository—which is curated, scanned, and seems to be as secure because the Play Retailer. However Aptoide additionally permits straightforward self-hosting of APK repositories for anybody who needs to add their very own—whether or not they’re a consumer eager to “again up” APKs which might disappear from the Play Retailer, or a developer internet hosting their very own authentic software program.
The convenience of repository creation on Aptoide—and the prevalence of pirated and cracked apps on its consumer repositories—makes incautious “procuring” by less-informed customers a extreme safety threat, significantly when these customers may not understand they’ve left the security of the mainstream within the first place.
Even customers not searching for pirated software program could inadvertently come across malware-added repackaging or copycat variations of official functions, with obvious “legitimacy” added by re-signing the modified or copycat utility with the uploader’s personal key.
Conclusions
Based mostly on the NCSC’s findings, there does not appear to be any challenge with the OnePlus cellphone—which comes as little shock, because it’s the one model of the three which hasn’t come underneath repeated, adverse scrutiny from non-Chinese language administrations.
Significantly adventurous and/or Google-hating shoppers may fairly be fascinated with Huawei’s P40, which appears bothered extra with a scarcity of malware-preventing guardrails than with precise immediately imposed censorship and/or adware.
Lastly, we would strongly advise avoiding the Xiaomi Mi 10T—its deactivated however commonly up to date blocklist performance strikes us as a warning of direct authoritarian oversight which shouldn’t be evenly ignored.
[ad_2]
Source
